Network Scanning With Nmap
You can now get MikroTik training direct from Manito Networks. MikroTik Security Guide and Networking with MikroTik: MTCNA Study Guide by Tyler Hart are both available in paperback and Kindle!
Preface
Regardless of whether you're scanning your own networks or not, someone else almost certainly is. It's a given that devices on the Internet are exposed to an active and ever-changing threat environment, and you're a part of it. Hackers, security research organizations, governments, and others regularly run port scans on large swaths of public IP space. Websites like Shodan.io index the results of network scans and make the results searchable for their customers. It's a given now that almost everyone on the internet is being scanned and targetted if they are determined to be a "soft target".
Given the current threat landscape the best thing to do is take an active role in the process - it's time to scan your own networks. One of the best tools to do it with is Nmap, which has been the standard in port scanning for quite a long time. The following sections will take you through downloading Nmap to running basic scans, and interpreting the results.
Authority to Scan
Before doing any network scanning it's important to first verify that you have the authority and permission to scan the network(s) that you're targetting. Oftentimes the only difference between a hacker and an auditor running network scans is how they are getting paid - the targets, tools, and techniques are often the same. If someone had no idea you were running network scans and you begin triggering IPS alerts across the network it will look like an attack, and someone working in IT Security or Information Assurance would be correct to isolate the source of the scans and begin investigating.
If you are scanning your own organization's networks be sure the rest of your team is aware it's happening so they can deconflict your "friendly fire" scans from real network incidents. If you are an auditor and scanning a customer's networks be sure that you have permission to do so in writing, and make sure that someone has your contact information so they can also deconflict your network scans from a possible network intrusion. If you are doing a Red Team assessment with a client make sure that there is an open line of communication from your point of contact, because the IT or IS department shouldn't know you're doing this, and they will most likely react as though it's a real-world intrusion if your port scans trigger IPS alerts.
Install Nmap
Installing Nmap is very straightforward and should only take a minute or two. There are two components: Nmap is the port scanner, and Zenmap is a GUI over the top of it. You don't have to use Zenmap, but it's included in the Windows installer and is easily installed on Linux as well. Ensure that you only download Nmap from the Nmap.org website or via official Linux software repositories.
Windows Installation
For Windows platforms visit the Nmap Windows download page and run the installer.
Linux Installation
Nmap is available via pretty much every software repository in mainstream Linux distributions:
APT
Install Nmap from the official software repository via APT:
apt-get install nmapYum
Install Nmap from the official software repository via Yum:
yum install nmapTypes of Scans
There are a few different kinds of network scans, each tailored to a specific purpose. Each different scan has a varying level of activity and rigor, and many times one scan helps define the scope of the next. Each kind of scan is shown in the table below, with the Nmap command to run it in the respective sections.
| Type | Rigor | Speed | Host-based IPS Trigger | |
|---|---|---|---|---|
| Ping Sweep | Low | Fast | Unlikely | |
| Port Scan | Moderate | Quick to Slow | Possible | |
| Service Scan | Moderate | Quick to Slow | Probable | |
| Compliance Scan | High | Slow | Likely |
All port scan commands are shown in command-line format, because they will work both at the command line without Zenmap, and you can copy-paste them into the "Command" field as well inside the GUI. It's important you learn how to use both the command line and the GUI if you're doing port scans often.
Ping Sweep
A Ping sweep is the simplest kind of scan, and has a very low impact on network performance. This kind of sweep simply sends an ICMP echo (ping) to each IP on the network and listens for a reply. This is great for determining which IPs are active in a network, and how many total hosts there are. Ping sweeps typically complete in fairly short times, and are unlikely to trigger a host-based IPS product because single pings don't normally appear malicious.
Unfortunately a ping sweep doesn't tell you anything about the devices responding to the echos, and if the hosts are running a host-based firewall that blocks pings they will appear to be offline (even though they aren't).
Nmap Ping sweep command:
nmap -sn 192.168.88.0/24Example scan:
tyler@manitonetworks.com:~$ nmap -sn 192.168.88.0/24
Starting Nmap 7.12 ( https://nmap.org ) at 2016-11-26 06:10 UTC
Nmap scan report for router (192.168.88.1)
Host is up (0.0011s latency).
Nmap scan report for 192.168.88.183
Host is up (0.0019s latency).
Nmap scan report for 192.168.88.184
Host is up (0.0063s latency).
Nmap scan report for ubuntu (192.168.88.196)
Host is up (0.00047s latency).
Nmap scan report for 192.168.88.253
Host is up (0.0042s latency).
Nmap done: 256 IP addresses (5 hosts up) scanned in 8.81 secondsWe now know that five devices are online, but we know nothing about them. This can help define the scope of future scans though.
Port Scan
A port scan is the typical scan for when you need to go a bit deeper than seeing just who is online. The typical port scan has a very low impact on network performance, though if you're scannning a lot of ports on multiple hosts in parallel it could have an impact if the network is already busy. A port scan could trigger a host-based IPS depending on the product, how quickly you're hitting ports, and how many ports are being scanned at once. TCP and UDP port scans have a fairly well-defined signature, and because hackers use port scans for reconnaisance they are flagged as malicious.
Port scans tell you what ports are open for each protocol, e.g. TCP port 80 would be found open on a web server. UDP port 123 discovered open means that NTP is running on a server. Normally in a port scan only open ports are reported, and ports that are closed are omitted in scan results. Filtered ports are shown because how a device responds on a filtered port can help fingerprint it.
TCP Port Scan:
A TCP port scan probes TCP ports, sending packets and waiting for a reply to confirm if the port is online or not. This method of testing if a port is online is fairly reliable due to TCP's connection-oriented nature, though it does create a lot of open connections that never fully complete. The -sT flag sets up a TCP scan in Nmap.
nmap -sT 192.168.88.0/24Example scan:
tyler@manitonetworks.com:~$ nmap -sT 192.168.88.1
Starting Nmap 7.12 ( https://nmap.org ) at 2016-11-26 06:27 UTC
Nmap scan report for router (192.168.88.1)
Host is up (0.0098s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
23/tcp open telnet
53/tcp open domain
80/tcp open http
2000/tcp open cisco-sccp
8291/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.19 secondsUDP Port Scan:
A UDP port scan sends packets to UDP services like DNS and waits for a reply to confirm if the port is online or not. Probing UDP ports is hit-and-miss due to UDP's connectionless nature - if a service doesn't actively reply on an otherwise open UDP port then it won't appear online. Probing TCP ports is easy because all that has to be done to get a response is sending a SYN packet, but UDP has no such handshake mechanism. The -sU flag sets up a UDP scan in Nmap.
nmap -sU 192.168.88.0/24Example output for this scan is omitted, because it looks much like the output of the TCP scan.
Combined Port Scan:
It's possible to combine protocol scans and specify ports to be checked. This scan specifically targets the Top 10 ports for each host on TCP and UDP protocols:
nmap -sT -sU --top-ports 10 192.168.88.0/24Scan results:
The output of this scan only includes two hosts for brevity.
tyler@manitonetworks.com:~$ sudo nmap -sT -sU --top-ports 10 192.168.88.0/24
Starting Nmap 7.12 ( https://nmap.org ) at 2016-11-26 06:41 UTC
Nmap scan report for router (192.168.88.1)
Host is up (0.0024s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp open ssh
23/tcp open telnet
25/tcp closed smtp
80/tcp open http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
3389/tcp closed ms-wbt-server
53/udp open domain
67/udp open|filtered dhcps
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
161/udp closed snmp
445/udp closed microsoft-ds
631/udp closed ipp
1434/udp closed ms-sql-m
MAC Address: 6C:3B:6B:05:CB:BF (Unknown)
Nmap scan report for 192.168.88.183
Host is up (-0.0076s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp closed ssh
23/tcp closed telnet
25/tcp closed smtp
80/tcp closed http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
3389/tcp closed ms-wbt-server
53/udp closed domain
67/udp closed dhcps
123/udp closed ntp
135/udp open|filtered msrpc
137/udp closed netbios-ns
138/udp open|filtered netbios-dgm
161/udp closed snmp
445/udp closed microsoft-ds
631/udp open|filtered ipp
1434/udp closed ms-sql-m
MAC Address: 00:6B:9E:85:C7:14 (Vizio)Service Scan:
This type of scan builds on TCP and UDP port scans, discovering the service versions running on individual ports. Finding the service versions and the daemons running them helps fingerprint a device, and is done through "banner grabbing" and scripts. Once we know the service versions it's easy to determine if any of them have vulnerabilities that have been disclosed. Hackers use this information to prioritize targets, which is why port scans are considered malicious unless done by a trusted insider or external auditor. The -sV flag specifies a service scan.
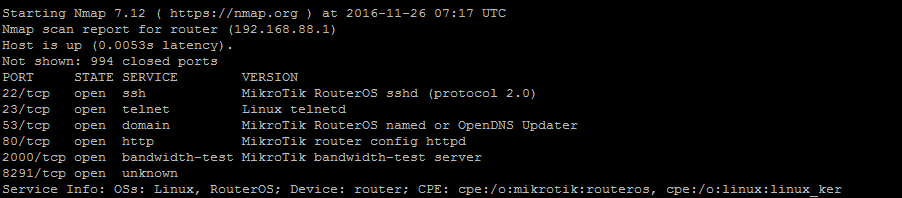
nmap -sT -sV 192.168.88.1Scan results, with some output omitted because it is shown above already:
tyler@manitonetworks.com:~$ nmap -sT 192.168.88.1
Nmap scan report for router (192.168.88.1)
Host is up (0.0093s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh MikroTik RouterOS sshd (protocol 2.0)
23/tcp open telnet Linux telnetd
53/tcp open domain MikroTik RouterOS named or OpenDNS Updater
80/tcp open http MikroTik router config httpd
2000/tcp open bandwidth-test MikroTik bandwidth-test server
8291/tcp open unknown
Service Info: OSs: Linux, RouterOS; Device: router; CPE: cpe:/o:mikrotik:routeros, cpe:/o:linux:linux_kernelIn this case we get a lot of output to digest. First, we're able to tell that the device is a router because it's running Mikrotik RouterOS. Secondly, we know that it's probably still running a stock configuration because all ports are open and all default services are running - no one has followed the Mikrotik Router Hardening Guide. Third, we can infer that the factory default credentials (admin:no password) are probably still in place because nothing else appears to have been tuned for security.
Compliance Scan
The next step after doing port and service scans is to run compliance scans for deeper insight into your security. In order to run these kinds of scans you'll need additional software - we recommend Nessus by Tenable Network Security. This software is able to run port and service scans, as well as log into your devices and enumerating patches and configurations. It can check against published vulnerability lists like OSVDB and Mitre's CVE list to determine if your hosts have vulnerabilities, and provide dashboards and reports to help you remediate systems.
Nessus is what Manito Networks uses for our clients, and it's also used by a number of defense organizations to help secure their networks.