Ping Sweeps with Metasploit
Need help with implementation or an upcoming project? We offer professional services at reasonable rates to help you with your next network rollout, security audit, architecture design, and more. Click here to find out more.
Port scans have a big role in network scanning and enumeration, but they are very noisy, and a blatant giveaway that network reconnaissance and enumeration is happening. IDS products have become very good at detecting port scans, and seeing those inside their networks put sysadmins on the alert (or at least they should). While it would be great to port scan entire subnets, we need to hold off and remain low-key at first.
ICMP echos (ICMP type 8) and echo replies (ICMP type 0) on the network don't raise questions in many environments, and inside many networks ICMP is allowed through firewalls because sysadmins want to be able to easily ping around while troubleshooting. With increased adoption of IPv6, which relies heavily on ICMP, this may become the case more and more.
For this exercise we assume you have Metasploit Framework set up or you're using Kali Linux in a VM, and have established a Meterpreter session with at least one host in a network. It doesn't matter how you established the session, either through an Excel macro or some other means. In my case I've created an executable with msfvenom and run it on a Windows 10 virtual machine, getting a reverse HTTPS meterpreter session back to a Kali Linux VM.
Initially compromised host
Right from the start we see that the compromised Windows 10 machine is in the 192.168.88.0 network. Interacting with the established session and running the ipconfig command reveals more about the network it's attached to.
Host IP Address
We see the IP address and subnet mask of the compromised host, and it's clear from the subnet mask that the host is in the 192.168.88.0/24 network. That means everything from 192.168.88.1 to 192.168.88.254 is open for port scanning. Chances are that the device at the top or bottom of the range is going to be the gateway, and everything in between could be workstations, printers, wireless access points, or something else.
We'll use the post/multi/gather/ping_sweep module to run a ping sweep through the established session.
use post/multi/gather/ping_sweep
Now set the ping sweep options, in my case using session number 1:
set rhosts 192.168.88.0/24 set session 1
We'll also set the Verbose option so we can see what the ping sweep is doing:
set verbose true
Run the sweep:
run
Here's what we see as the scan runs, then completes:
Running ping sweep
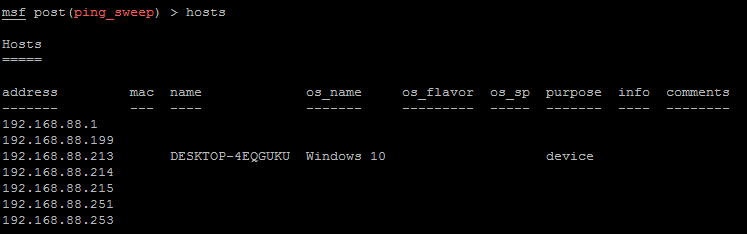
Sweeping a /24 network only takes a minute. Let's use the hosts command to view what hosts we've found:
Discovered hosts
Comparing this hosts output with that shown at the beginning and we see the newly discovered hosts. From this point we can move on to targeted port scans to identify the platforms and services running on the network.