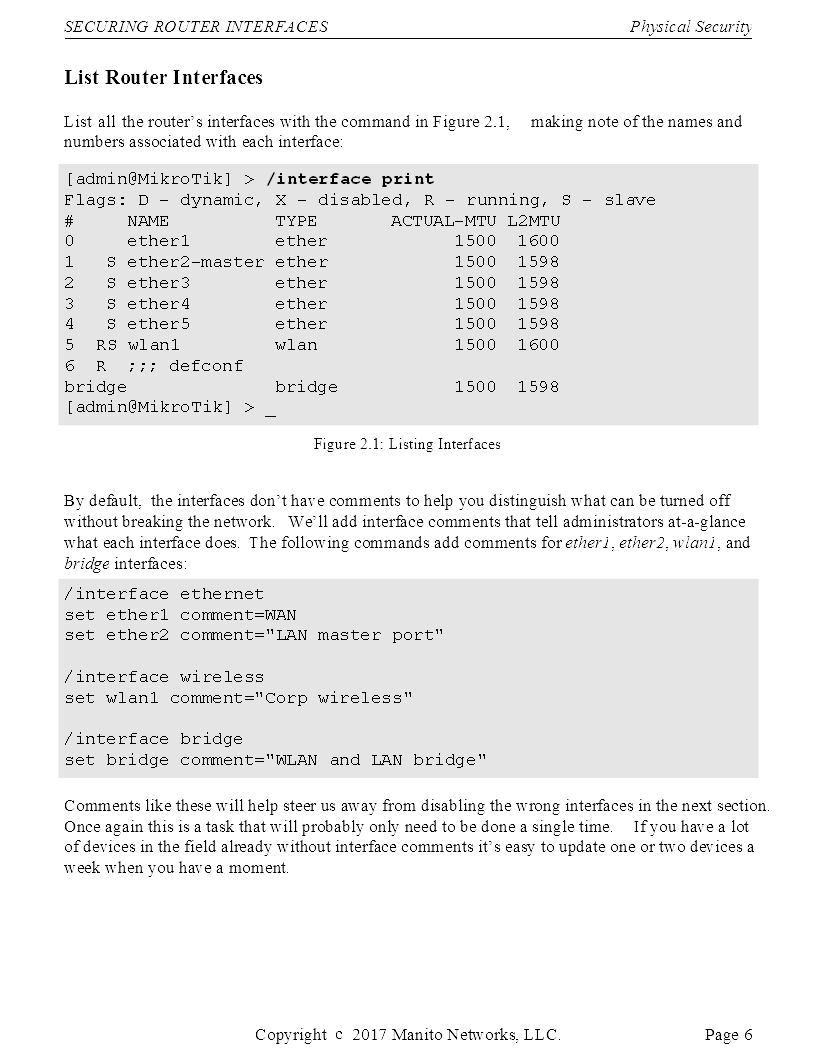
MikroTik Security Guide



MikroTik Security Guide
MikroTik Security Guide, Second Edition, is the definitive guide to securing MikroTik RouterOS and RouterBOARD devices. It's built around industry best practices, legal and compliance standards, and lessons learned by the author during years of auditing and consulting engagements. Links to industry-standard best practices and STIG documentation are included to help enhance your MikroTik network security program.
Topics include physical and wireless security, locking down IP services, managing users, configuring firewalls, segmentation with VLANs, and more. Chapters include simple to follow descriptions of how and why steps are performed, and easy copy-paste commands you can run directly on your RouterOS devices. Many of the topics included in the guide also correspond with MikroTik's MTCNA certification outline, so it's great for on-the-job use and professional development.
The Guide
The MikroTik Security Guide, Second Edition, is over 100 pages of real-world information with commands and methodologies for securing RouterOS devices. It's built around industry best practices, legal and compliance standards, and lessons learned by the author in auditing and consulting engagements.
Sections
The guide includes the following sections:
- Using Safe Mode
- Physical Security
- Interfaces
- LCD Touchscreen
- Console Ports
- Physical Spaces
- Services
- Network Scanning
- Securing IP Services
- DNS
- Neighbor Discovery
- MAC Services
- Bandwidth Test Server
- Strong Crypto
- SNMP
- Firewalls
- Chains
- Rules
- Actions
- States
- Input Rule Set
- Forward Rule Set
- Best Practices
- User Management
- Default Accounts
- Managing Accounts
- Centralizing AAA with RADIUS
- Best Practices
- Software
- RPF
- Login Banner
- NTP
- Backups
The Author
Tyler Hart is a networking and security professional with 15 years experience. He holds a Business degree in IT Management, as well as the CISSP credential and others from Microsoft, CompTIA, Cisco, (ISC)2, Tenable Network Security, and Kitco. Over the years he has worked and consulted with large and small organizations including hospitals and clinics, ISPs and WISPs, U.S. Defense organizations, and state and county governments.