Alert Notifications in Windows with MSG
Need help with implementation or an upcoming project? We offer professional services at reasonable rates to help you with your next network rollout, security audit, architecture design, and more. Click here to find out more.
It seems like such a silly thing, but pop-up notification messages can be very useful. They can be used as a super quick proof that you're on a system ("Hi Customer XYZ"), and in social engineering engagements to trigger some kind of response. Notifications can augment an exploit running in parallel, feeding a user false information or giving directions while something runs in the background.
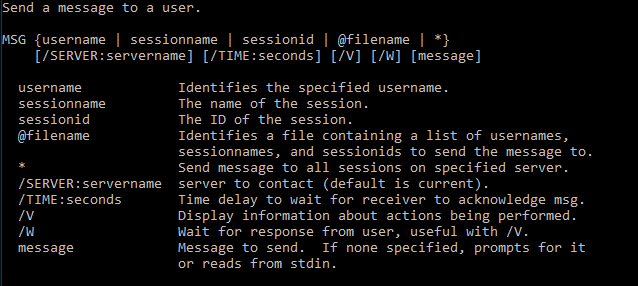
The great thing about basic Windows pop-up alert messages is the tool used to send them - msg. The msg command can send a text string you type in manually to an alert message, or it can read input from a text file. This command also runs on pretty much every version of Windows out there, all the way up to the latest Windows 10 version as of September 2016.
If you're able to get shell access on a Windows machine, simply try the following command:
msg * "Hey there!"
And there you have it - a little pop-up alert. The asterisk means the message will be sent to all running sessions and users on the machine, and the text is there in quotes. Msg also has other options, which you can see using msg /?:
It's also possible to input the contents of a text file into msg using < as shown below:
msg * < C:\hacked.txt
Now you won't have to type a longer message manually, and it removes the chances of fat-fingering command input. Here's an example of msg output:
Windows msg command alert
That's all there is to sending basic notifications!
With all that being said, the basic command line msg is crude compared to creating notifications with Powershell. If you want to take things up a notch give that a look.